The headteacher received an… interesting email from an anonymous email address. The content of the email was supposedly saying that a number of students had been witnessed doing things they shouldn’t be doing, and that the person who sent the email did not wish to be known (yes, I am aware that’s the definition of anonymous). I only know all of this due to the headteacher asking me to have a look at the email and to find out which student may have actually sent it (yes, I did point out that the email was anonymous). “Not an easy task“, you may say. “Impossible, even“, and you’d be right. “Only an absolute genius could figure out which student sent the email“, oh, well, OK – I’m going to hold you to that…
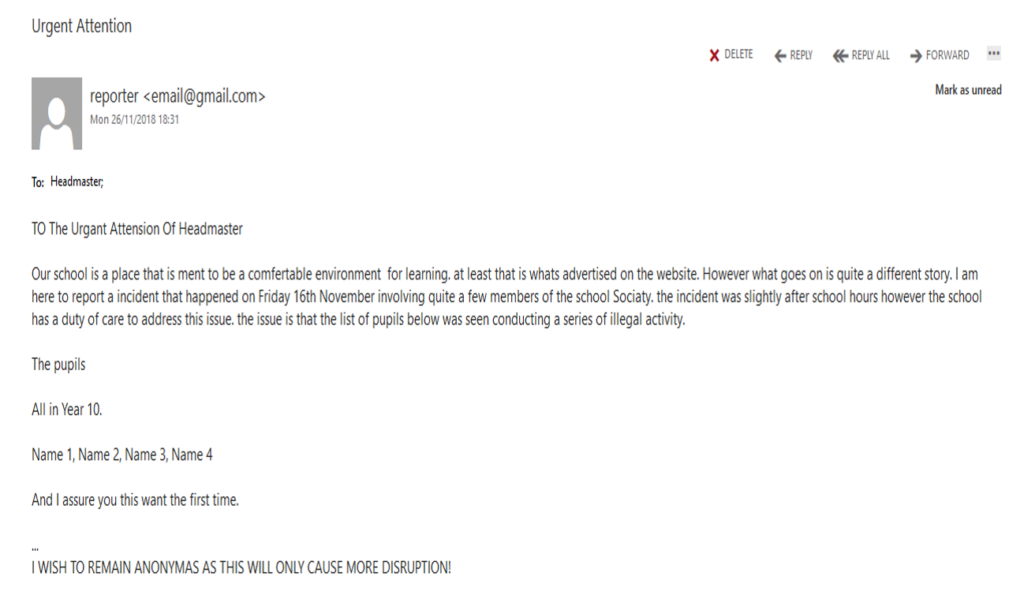
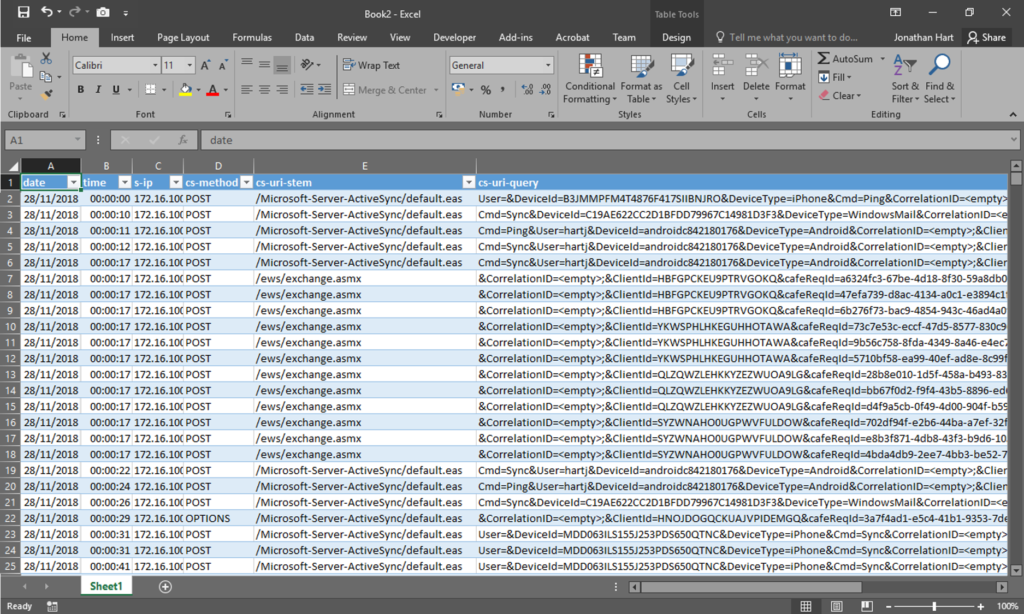
Here’s what I had to go on: the time of the email when it was sent, the sending email address and the recipient email address. Very little information but I needed to start somewhere. My best guess, main hope and instinct was that the student would have logged into their school emails around the time the anonymous email was sent. We use Microsoft Exchange on-premises as our email server, which uses Internet Information Services to host the files. I browsed to the log file storage location on the server, opened the log file from the date the email was sent, and imported it into Microsoft Excel to see what I could find.
Pro tip: I used the text to columns option to split each line of the log file into the relevant columns, then converted it into a table so it could be filtered easier
I knew the time that the email was sent, so I deleted any log lines that were outside half an hour each side. From there, I removed any staff members that had been using our email system (I had assumed that it wasn’t a member of staff who sent the email), which left me with a filtered list of 13 students who had used our email system within that timeframe. I presented this list of potential students to the headteacher, and there were a few names that were noted as being people who may have the intent to send the email. I left this list with the headteacher, so they could do some more investigating, and carried on with my day.
“That’s all well and good” you’re probably saying to yourself now, “but does it really make you a genius? You came up with a list of 13 students, not said which student it was exactly, which is what you said you would do!“. Well, prepare to put mustard on those words.
If you want to try and be anonymous, you should never send the same message twice. It’s how smart people we were able to break the Lorenz Cipher, and if those smart people were able to do it, then I could identify who sent the email (admittedly, I wasn’t dealing with ciphered text, but the principle is the same). It seems the student that had sent the original message had noticed that nothing was being done to the students who had been “named“, so they send the same email again. This was their first mistake.
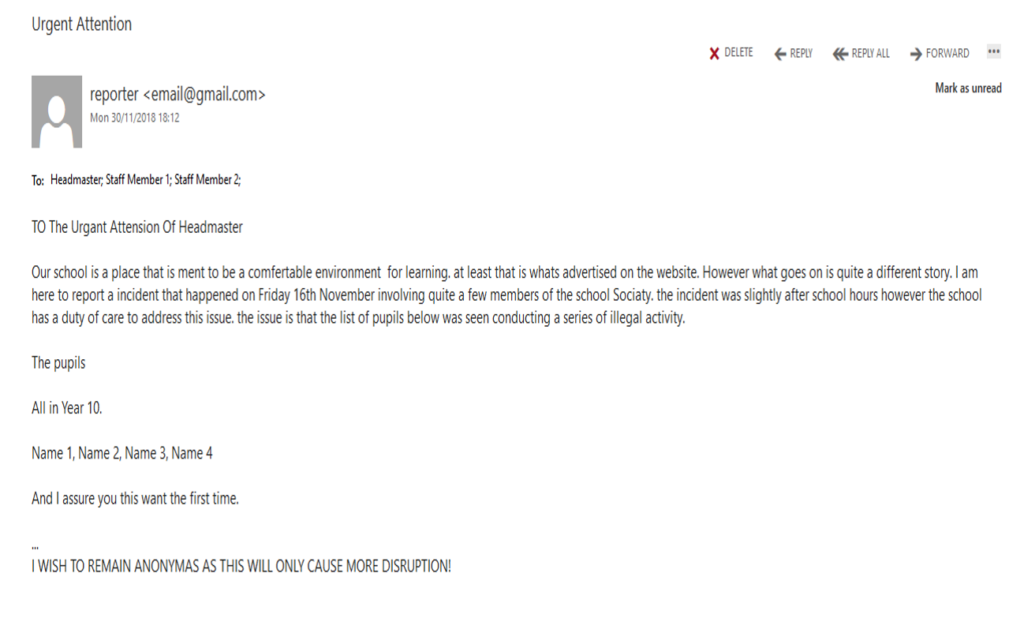
Still going on my hunch that the student would have logged into their school emails around the time the message was sent, I copied the relevant log file from our email server, imported it into Microsoft Excel and filtered it to student accounts that were active half and hour each side of when the message was sent. I was left with a shorter list of students this time. The benefit of having two lists what that I could now compare them to see if there were any students that appeared in both lists. There were two names left after doing this.
Of the two names, one was a student who was in the winning team of CyberCenturion from last year, and one was a student who’s stolen components from inside our computers in the past (let’s just say that following that incident, the school now has a Google review saying “their computers are bad especially the ram“). Either of these students could be capable of sending this email (it’s just an email, after all), and it could have all just been a complete coincidence.
Speaking of coincidences, the student who was part of the CyberCenturion team came to my office to ask me something, so I took the opportunity to ask if they’d been using the school email system when the messages were sent (to make sure I’d got the time ranges correct). I also asked if they’d been sending any emails recently, to which they wondered why I was asking. I said that I was investigating something and that I’d let them know sometime in the future (i.e. when they get to this point in the blog post).
I handed the headteacher the two lists of students who had been using our email server when the emails in question were sent, along with the narrowed down list of students. I couldn’t guarantee that the students it had been narrowed down to were the ones who sent the email, they could have just been using the email system at the same time, but we both knew that it wasn’t the student who was part of the CyberCenturion team. I left the headteacher with the new lists for him to carry on with his investigation of who sent the email.
“You said that you’d be able to narrow it down to one student!“, I hear you now exclaiming, “You’ve made me read all of this so far on the belief that I’m going to end up praising you about how amazing, awesome and clever you are, but all you’ve really done is made me waste my time“. Well, if I may interject, you’ve clearly not been paying much attention. I said earlier that the first mistake the student made was that they sent the same email twice. What you haven’t let me get to yet is their second mistake.
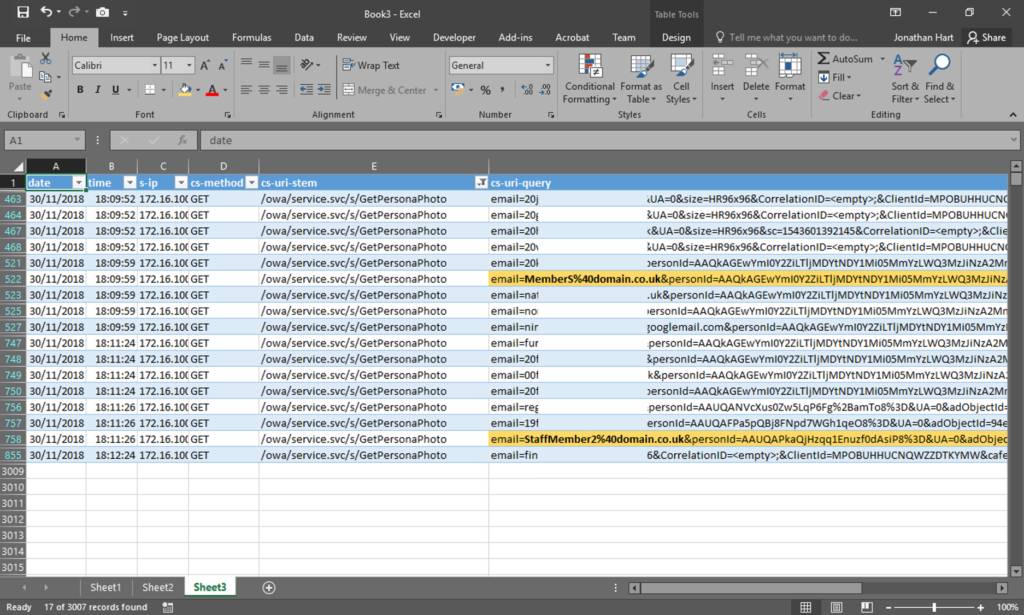
The second mistake was that when the email was sent again, the student included two other members of staff as recipients (most likely to try and get their message across). The staff email addresses all have the same format, which is the staff members surname and first initial, e.g. Arthur Aardvark would be [email protected]. However, a number of years ago some members of staff had incorrect email addresses created for them, which consisted of their full name followed by the number 2 (e.g. [email protected]). While the email addresses have since been corrected, I still need to keep the incorrect ones around so that email can still be delivered. The inadvertent benefit of this is that when searching for certain members of staff, the old address can be shown. Now, take a guess at which email address had been used for one of the email recipients…
One of the fields available in the logs from IIS is the request URL. When performing a search to find email addresses via OWA (take your pick from Outlook Web Access, Outlook Web App or Outlook on the web), a query is sent to /owa/service.svc/s/GetPersonaPhoto, to collect the users avatar image, and one of the parameters to this request is the email address of the user.
I performed a search for the old-format email address that had been used, and one result was found. Scrolling across to the column that contains the username of the person who performed the request, it was logged for one of the students who was on the narrowed down list – so far so good. I then changed the filters on the spreadsheet to look at just that students activity, along with any email lookup searches. It showed the other member of staff who had been emailed had been searched for too. Finally, both of these searches were performed a few minutes before the email was sent to them.
I had a quick look at the previous log file to see if the headteachers email address had also been looked up before the email was sent – it had been. I took this new information to the headteacher and said that I could guarantee the student in question had indeed sent the emails (well, assuming his password hadn’t been found out by anyone else!). The headteacher thanked me for my time and said that he’d speak to the student about why they’d sent the emails in the first place.
A day later, I was told the student had admitted to sending the emails. I didn’t find out why.
“Wow!“, I’m hearing you proclaim, “You really are an absolute genius!“. But wait … what’s that you say? “Why is the title of this post ‘My Proposed New School Motto’?“. Well – here’s my favourite part from the email:
As a right respecting school you should have an extreme duty of care to exterminate people
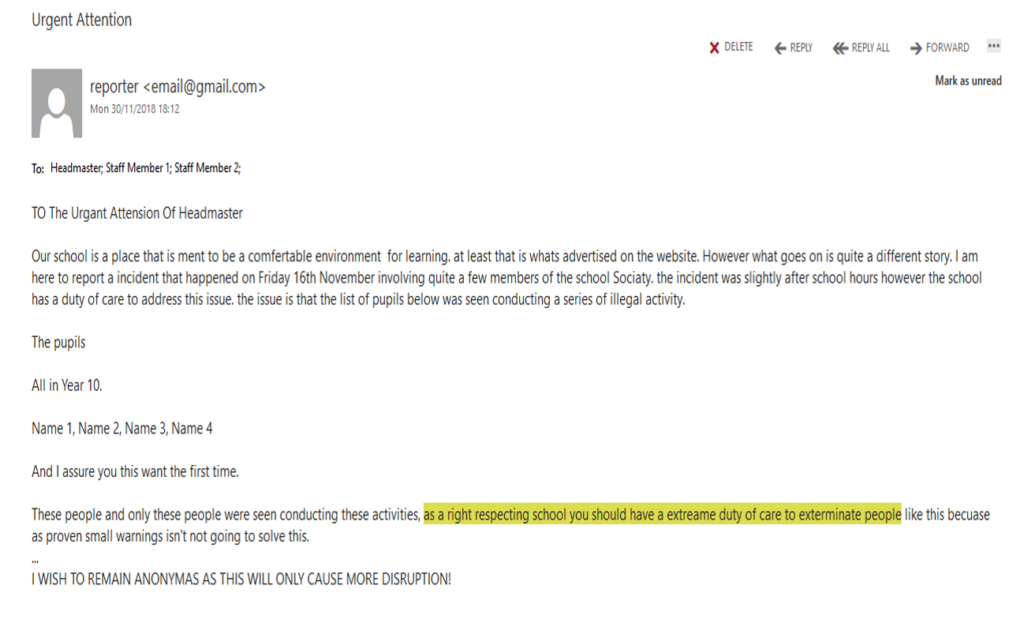
Guess who’s first on my list…