They’re still going on about the hurricane. Well, I suppose that is the only major weather event going on at the moment so there isn’t much else for them to report on. The presenter was showing some images of contacts in local areas and said “… and it’s important that you [gets cut off due to adverts]”. When he comes back on, nothing is said about that!
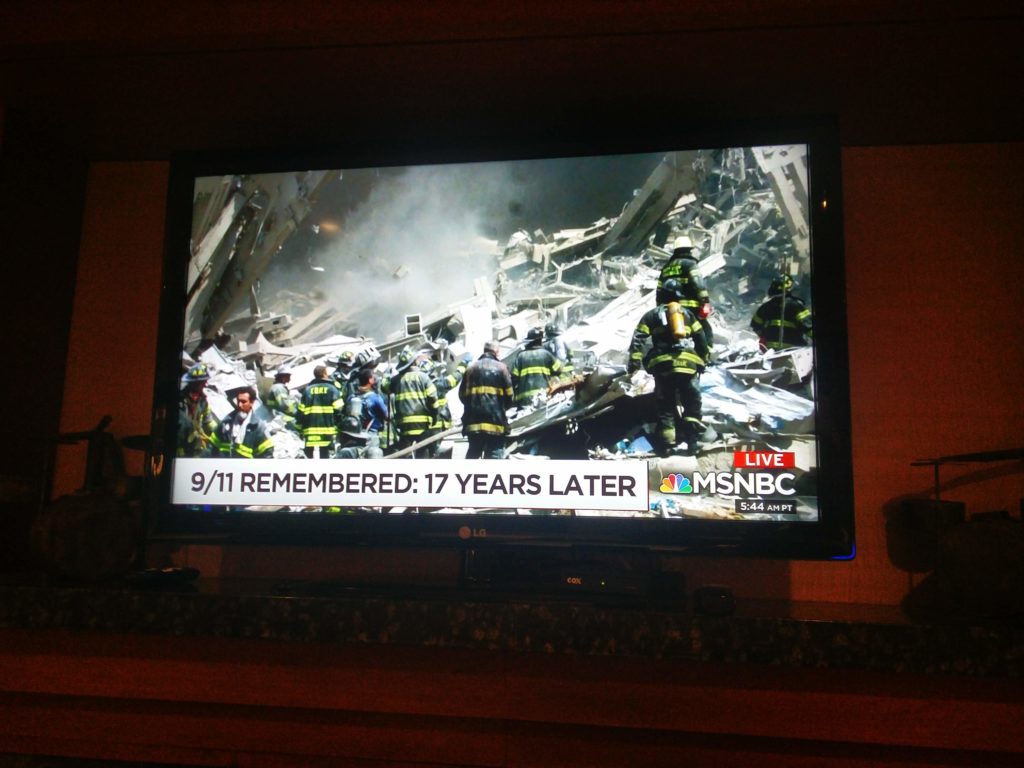
We went down to breakfast at quarter to 8, and managed to get things sorted properly this time as we knew what to do. We had a call from the minibus company at 9 o’clock asking if we were ready to be picked up, as somehow the times had been mixed up. We finished our breakfast and met up in the reception area for quarter to 9 to board the minibus. While we were waiting in the reception area for everyone to turn up, the TV in the lobby was showing the (actual) news channels, which are talking about the September 11th attacks due to it being the anniversary of them happening. A minute silence was held in respect to those who lost their lives from those events, which was a sombre moment. To put all of this into reality, it’s been 17 years, and some students with us on the trip hadn’t even been born yet. I’d also been in New York a few months before on holiday too, on the top observation deck of the World Trade Center tower, and that was the last time I’d been to the United States until a few days ago.
Once we boarded the minibus, the driver said that it would take about an hour to get to the Cyber Security Operations Center, so we settled in for the journey. And what an eye-opening journey this turned out to be, especially the amount of drivers who were using their mobile phones (sorry, cell phones) while driving! It’s against the law, and I’m sure that the police could make a nice tidy profit in just one morning had they been out catching people. We also saw numerous UPS vans where the drivers door was wide open (so they could get in and out quickly) while doing the speed limit (read: going fast!). Finally, I saw a cell phone tower that, let’s just say, could probably blend in quite a bit better with the environment.
We saw the Northrop Grumman building as we turned up to the technology park, but we were taken to the building on the opposite side of the car park. The driver checked what address he had been given and he confirmed that it was the building we’d pulled up to. We got off the minibus and went into the lobby of that building, but it turned out it was indeed the incorrect building. We went out of that one and walked across the car park to the Northrop Grumman building where Diane was waiting outside. She apologised for the mistake, went into the building and waited at the security desk. There was 8 of us, as well as a few other people, so we’d made quite a bit of a queue waiting to go through security. We were handed security badges that said we were visitors and had to be escorted around the building. Diane said that she’d forgotten her badge today too, which is only the fourth time in 33 years. We were escorted along a corridor, only to be told that we would be going to an auditorium first. [Looking back at it while writing this us, it wasn’t exactly the smoothest arrival we’d done].
This room had the same blue lighting scheme as the Innovation Center that we went to yesterday, and there was a wall with 3 projectors showing a computer screen. Around parts of the room there were computers and we sat at some long desks. The first presentation was by Nathan and he was the manager of the Cyber Security Operations Center. He gave an interesting presentation about how a team of 17 people protect the whole of the Northrop Grumman enterprise network (although after logging in he had a message pop up on his screen saying a BIOS update was available and would be installed in two hours). Nathan originally had a marines background, and had been one of the guards who stands next to the presidential helicopter. He mentioned that he had been to Birmingham in 1998 when Bill Clinton took a tour there. He also explained that before he started working in defensive security, he took part in offensive security with a government department seeing how their networks could be broken into, to then apply that knowledge so the networks could be tightened up meaning bad actors couldn’t pull the same tricks.

Now, he instead protects and defends networks. There were about 350,000 endpoints, 1,400 individual networks and a few hundred servers making up the infrastructure of Northrop Grumman, along with 80,000 employees. He explained how they first take a baseline assessment of networks and then use that to identify any problems. When an issue is identified, they can completely brick a device so the threat is contained on it to prevent it spreading over the network. They also perform phishing attempts themselves, directed at the employees, to identify where training may be needed and to raise staff awareness of what to look out for. For any email that comes into the company, they prepend “EXT” to the subject line, and free email accounts that have zip and pdf files attached have them stripped and any links contained within them can be blacklisted. Employees are encouraged to send emails to the team at the CSOC to help identify threats, and last year 245,000 emails were sent that had to be sorted through by the small team. The team works in 3 shifts, doing 10 hours a day for 4 days in a week. The weekend slots are then allocated as needed.
Nathan continued to explain how they collate data from a large variety of sources using Splunk (Active Directory logs, Anti-virus logs, web server logs, database, VirtualBox, Python, Virus Total, FireEye, etc…) and analyse it to find problems. Should they find any, they can reach out to other defence companies in similar businesses or the Department of Homeland Security to see if they have had the same happen to them and what they did to remediate the issue, or if it’s a new threat, to let them know what is happening and what they are doing. He also showed how a small project to save the CEO having to send spam emails to them due to FireEye not identifying it, they found another product (YARA) that could help identify spam emails, create rules based on the content and feed them back to FireEye to filter them out in the future. Occasionally this goes wrong with a false positive, and they get a call from the secretary of the CEO to say they’re expecting an email from a defence department or NASA and could they bump it through the filter quickly(!)
We were then told we could have a look at the center itself, but to leave our phones in the auditorium as we wouldn’t be able to take them in. We were escorted down a corridor (the one we started to go down when we were escorted after the security desk) and through a door. We went past Nathan’s office and went into the CSOC. I’m not sure how much I can say, but there were TVs on the wall showing CNN and there was a wall made of 9 displays showing a basic display of status of various important services (Internet, proxy, VPN, etc…). The desks themselves where people were working was in the form of a traditional cube farm, although all computers were set up in a triple monitor setup. Also in this room was a meeting room, where a meeting was going on.
Upon leaving this room, we walked past some of the system administrators, and they had a sign on it saying “system administrators in their natural environment“. Let’s just say that I’m going to be putting a similar sign up in my office when I get back. After that, we headed back to the auditorium. This is certainly the type of job that I’d like to do, as it’s similar to what I do at the moment, and you get to be the people in charge of things and not just having to conform to what has been set up. (I’m not power mad. Honest.)
It was then turn of Bill to do his presentation, which was about cyber counter intelligence. This involved him looking at a large amount of data and investigating whether it was a credible threat to the company or if it was just someone doing something slightly out of the ordinary (he mentioned an employee suddenly copying lots of files, but this was due to then leaving the company and was transferring personal photos of his kids from his work phone). He explained how affidavits prove helpful to his work, as they contain lots of information to help identify bad actors. He showed a few examples of this, such as the Y-20 Heavy lift aircraft, which was almost a carbon copy of the United States American Military plane, the C-17, that the Chinese now had. In relation to this, he showed another case study of an employee at Rolls Royce who was allowing the Chinese government access to their network so that they could steal information to make their own heavy lift engines, as they were currently using Russian ones.
Bill continued his presentation by showing a number of tools and websites (Threat Crowd,
Domain Tools, Risk IQ, Hybrid Analysis) that he uses to identify domains from when one is published as a phishing site. From there, he is able to see additional domains that reside on that IP address and also what malicious websites are set up on those. He also mentioned a few books that provide information into monitoring networks to help notice threats and how to mitigate them.
After his presentation we had lunch, which was sandwiches. These were in ciabatta bread, fresh ingredients and had a very big and filling. While this was happening, Bill was still around so we had a chance to ask him questions. I enquired how he came into this profession, as he didn’t start off with it. He said that he was in the army, and found that he was having to do more intelligence, such as sending troops in to an enemy base, scanning their computers and pulling as much info out of them before using this information on where to go next. Once we finished lunch, we thanked Bill, handed in our badges and went back to the minibus (which was parked up opposite the original building we were dropped off at).
We were now heading to the National Cryptologic Museum, a separate building to the National Security Agency but linked to it. This wasn’t too long of a journey, and we got a chance to see the NSA building as we went past. There was a large police presence there, and also a surprisingly large number of cars in the car park.
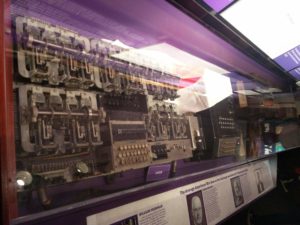
We went into the gift shop first, as we had a tour scheduled for half 1 to half 2. We met up with Ken, who was a former NSA employee but now worked with assisting with the museum since retiring. We were taken to a few exhibits, such as the Enigma machine and he explained how various people started to work on deciphering the codes it produced. We also got some back story about the Enigma machine, that it was originally developed but didn’t have much uptake as people couldn’t see a need for it. When the Nazis came to power though, they prevented any further manufacture of the machine and used it for themselves. As the codes were starting to be broken, additional wheels were added, and this was seemed impossible to crack. However as German operators were testing out the machines when they were being handed out to the naval ships, they used it in the four wheel configuration, but to make sure that it worked correctly, they also sent the same message with three wheels in use. This then allowed the allies a way into cracking the code. We also got to see a Bombe which was a machine that would generate likely keys for the allies to use. It was also explained how America and Britain agreed to work together with the people at Bletchley Park to help decipher the codes.
We then walked through to look at Japanese variations of the Enigma machines, named Purple by United States code breakers, as well as previous versions of the machines. The codes generated by these machines also needed to be broken, all without knowing what the machine looked like. Once the wats were over, a person who worked on the original machines came to look at the designs that had been used to create machines to help break the codes, it was found out that there were only 3 wires in different locations.
Another exhibit that we looked at was Navajos and how their spoken language isn’t written down anywhere, so they are used by American forces, knowing that whoever may be listening in wouldn’t be able to decode the messages. One of the reasons for this is that there are 10 words that mean the same word in English, and if they needed to say a word that wasn’t in their native language, they would instead spell the word out by using the first letter of their words and string them together to make a long-sounding message, that may actually only consist of just two words in English.
We then carried on around the museum to the electronic versions of machines that were used to break more advanced codes. We saw a Cray machine that helped speed up calculations (but which had a horrible wiring loom). We saw some machines that the Allies used to encrypt our messages, but needed to be unbreakable by the opposition. One of these clever machines that was created was called SIGABA, where there were 15 rotors that could be placed in any location, any start position and even backwards. Other rotors would the shift the wheels into random positions.
We got to see a model of the Bell Labs machine called SIGSALY that would encrypt spoken telephone communications so the President of the United States and Winston Churchill could talk securely. The encryption was generated by a record playing random noise and combining it with the spoken words. At the other end, the same record was played, within a 1000th of a second, so the message could be decoded. The final part of the tour went into details of more recent history (well, the Cold War) and how the Russians had offered a gift to the United States ambassador of a wooden carving of the Great Seal of the United States. However, quite a while later it was discovered that there was a listening bug (called “The Thing“, which is a great name however you look at it) hidden inside the seal and spies were able to listen in to conversations happening in the ambassadors office by pointing a transmitter to provide power for the device, which in turn would send live audio back. After that the tour was over and we made our way to the National Electronics Museum.
Near the museum there was another Northrop Grumman facility that Diane said was used to create some of their products. We pulled up to the museum and got out of the minibus. Outside of the museum there were a number of large radio devices, and after we went through the entrance doors, we were greeted by Daniel, who was going to be giving us our guided tour.
The museum was divided into various sections, and we started in the Fundamentals Gallery (by virtue of it being the first gallery you entered). Daniel showed us a number of exhibits (most of which were hands-on) and explained how the findings from these early experiment and pioneers helped set the foundations for everything else that we would see. Some of the exhibits that we saw in the room were a Jacob’s ladder, a very early radio and a large selection of vacuum tubes.
We carried on to the next room, to the Communications Gallery, which introduced you to items that were are the forefront of enabling mass communication over large distances, from a Morse Code telegraph to a reproduction of the early radio equipment that Marconi was working with. The students thoroughly enjoyed playing with the telegraph (it’s amazing what will keep them entertained) and I was fascinated how moving a loop of wire through magnets (a very little else) allowed a magnetic detector to pick up radio signals.
Daniel then took us to the next room on our tour, which was based on radios, radar and their use during the Second World War. We saw some of the early versions of these machines, which had hundreds of vacuum tubes and were the size of a lorry. The antennas for these were also very large, with one having to be located outside the museum simply due to it not being able to fit in the room. We were also told of an interesting story of when radar was in its early days but had been deployed in Hawaii. As people were still getting used to how this technology worked, two army privates were meant to shut down the receiver at 7 o’clock, but instead kept it on to gain more experience. A few minutes later they detected a large echo and reported it. However, this was misinterpreted as American aircraft returning, rather than the Japanese Air Force on their attack run of Pearl Harbor.
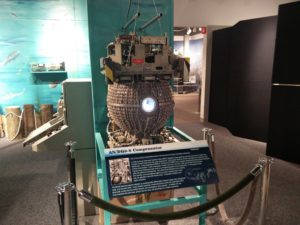
Carrying on through the museum, we were then in the radar galleries for the Cold War through to modern day. These included a large number of Doppler receivers and how they were used to detect incoming missiles, either on the ground or on planes. On the wall is an antenna from a Boeing E-3 Sentry plane which was damaged during maintenance. We were told that this fell off a fork lift truck when it was being moved, and despite there only being two small dents in the array, it was more practical to make a brand new one than try and have this one repaired, so the museum managed to get hold of it as an exhibit.
After seeing all of these exhibits about detecting enemy aircraft and missiles, the next part of the museum that we saw was related to countermeasures, such as radio jamming (sorry, this type) and using decoy items to confuse tracking systems, called chaff. These were needed to be developed by the fact that enemies were also developing their own radar systems, so we needed to find competitive advantages. Modern war aircraft now carry a variety of electronic countermeasure devices, attached to their wings, which help them evade most threats while in enemy airspace.
The next room in the museum contained both the underseas and electro-optical galleries. For the underseas gallery, it showed how some of the technologies that had been developed for use in the air could also be utilised under the sea, either for mapping the sea bed or identifying submersibles through SONAR. For the electro-optical exhibits, these showed how the use of laser lights could help guide missiles to their intended targets and how aircraft can be built stealthily. Additionally in this room were two cameras, one normal full-colour spectrum and one infrared. These cameras were pointing at a selection of materials, and were used to show how thermal “marks” could be left behind and how a non-reflective metallic surface in visible light acted as a perfect mirror when using the infrared camera.
The final gallery that we went into was related to satellites and how they have made an impact on our lives, from GPS to providing Internet connectivity in remote locations. It also had a display of the impact that we are currently having around our planet from the amount of space junk that has been left lying (well, orbiting) around. Additionally, there was information about the rockets that are and have been developed to help put satellites into orbit.
Our tour was now finished (it had been over an hour!), and everyone thanked Daniel who gave a great tour and was very insightful. We also commented on how many exhibits the museum had and how interesting they all were. However, most people were quite tired at this point, as we’d been standing quite a while. We decided to go back to the hotel and have food at the local mall again. We waited for the minibus to come and collect us and all got on. As we started our journey, we were surprised to see another Northrop Grumman building right next to the museum!
This journey took quite a while longer than going, simply due to it being rush hour. Even with four-lane and larger roads, there were still quite a number of delays. We were however able to entertain ourselves by looking at the sheer number of drivers who were using their phones while on the move, sometimes with both hands off the wheel on a freeway! There were even some people who were watching films on tablet devices while driving. Seriously USA people… put these devices down and concentrate on your driving. Sorry, rant over. On our way back to the hotel we dropped Diane off at the offices where Innovation Center was located.
At the mall the students went off to have food in the food court (so they could have a choice of food) and the other staff members and myself went to TDI Fridays again. This time, due to the lack of students, we went up to the bar to order drinks (I had my passport this time, so no probing questions into my age) and we went to sit down at an outside area of the restaurant (although it’s still inside the mall). The main reason we did this was for the students to be able to see and find us. Unfortunately this happened too quickly, as the students had finished their meals before we’d even had ours, but they were more than happy to go on a walk around of the mall to pass the time.
When it was time for us to be collected, it was my turn to call for the minibus on the basis of me being forced to taking part in what we’d been told employees are told at Northrop Grumman, to always challenge themselves. Well, it wasn’t so much of a challenge making the phone call (that was a lie, it took me three attempts due to international dialling codes not working) but instead asking for us to be picked up – this went about as well as when we tried yesterday and couldn’t describe who exactly we were or what entrance we needed to be picked up from. I must’ve said something right though, as we did get picked up.
Once we arrived back at the hotel, we went over the arrangements for the following day. We would be travelling around some of the famous sights in Washington DC and be visiting the International Spy Museum in the morning, and during the afternoon we’d visit the British Embassy to talk with some of the staff who work there advising on cyber security and liaising with the American government. After that, everyone headed up to their rooms for the evening.
It’s certainly been a busy day for everyone today, and I’m falling asleep here lying in my comfy bed while trying to write up what we’ve been up to and watching the weather channel. Need I say that they’re still going on about the hurricane? Still, there’s been some developments during the day. For some evacuation routes, the police have blocked off entrances for some interstates and are allowing traffic to travel the wrong-way down highways to aid the evacuations.
Oh, I’ve just looked at what the weather may be for our sightseeing tomorrow. I think I may need my umbrella…